The more popular a new technology gets, the more likely it is for scammers and hackers to show up and try to take advantage of the loopholes in its system. This is an age-old story that has repeated itself over and over again throughout the years, and it appears to take place right as we speak in the crypto industry.
The crypto market has definitely had its share of ups and downs over the years, but recently, because of multiple internal (the emergence of NFTs for example) and external factors (celebrities getting into the industry), the cryptocurrency market capitalization has been on a steep rise, to say the least.
With this rise in popularity though we’ve also seen a steep rise in a brand-new type of threat, known as cryware.
What Are Cryware Attacks?
Cryware is the term that is now used to refer to information stealers that attack non-custodial cryptocurrency wallets, which also go by hot wallets. These individuals gain access to your hot wallet data and then they transfer all of your money directly to their wallets. Sadly, this is irreversible a hundred percent of the time, due to the fact that while on the blockchain, any transactions are final, you can never trace back where your money went off to and you can never ask for a refund.
How can they do this though? Essentially, data stealers can do this by clipping and switching, memory dumping, scams, phishing or they can just simply use simple word matching or regular expressions methods to gain access to your hot wallet.
New Malware and Crypto Attacks
Microsoft themselves have issued multiple statements discussing these new attacks and how they’re planning on fighting back against them. Amongst the most commonly found threats that you’ll have to deal with you have the following:
- Cryptojackers
This form of threat emerged way back when cryptocurrency first came about. We know that in order to farm cryptocurrency you need to use your computer’s resources, and as such, these cryptojackers will use mining malware which takes over your device and uses its resources for their gain without you even knowing that it’s happening in the first place. We’ve had several millions of cryptojacker reports last year alone, which means that although it is quite an old issue it is still prevalent to this day.
- Ransomware
This type of threat involves you being hacked and then blackmailed into paying a ransom payment to the people in charge of the attack.
- Password and Info Stealers
There are plenty of ways that hackers can make use of to hack your data, with their main target being sign-in credentials, keystrokes, and even your system information as a whole since this can all be found on your hot wallet data.
- ClipBanker Trojans
Trojan malware used to be very commonly found in the past as the virus would check your clipboard and steal all of your banking information amongst other such sensitive data. Nowadays the malware has also been updated to monitor your cryptocurrency addresses also.
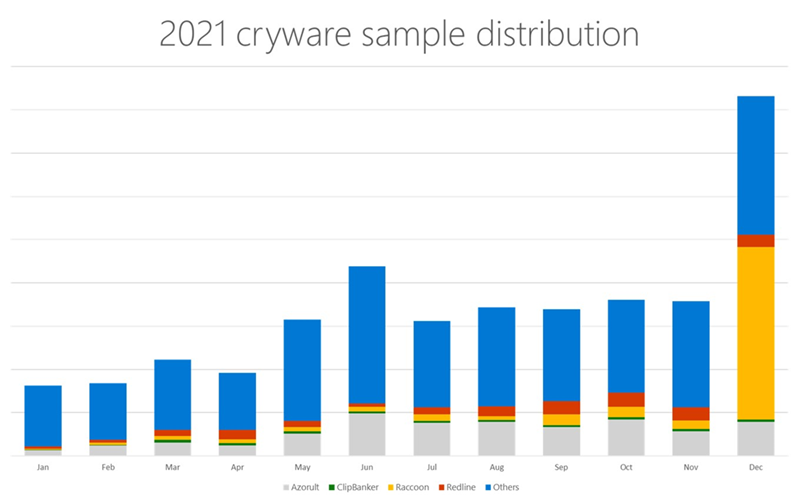
Source: Microsoft.com
Defending Against Cryware
As of 2021, according to Microsoft themselves, cryptocurrency crime has reached an all-time high, with well over USD10 billion worth of assets having been taken over through the use of ransomware and other instances of cryptocurrency theft. While we do still believe that cryptocurrency trading is still a largely positive and beneficial practice, it can also be quite risky to take part in these days. To combat this threat, Microsoft has created several means of protection, including the following:
- Microsoft Defender Antivirus
This app is meant to offer you protection, detecting instances of cryware, cryptojackers, and pretty much any other cryptocurrency-related threats out there.
- Microsoft Defender SmartScreen
This tool can be found on Microsoft Edge amongst other web browsers out there, defending your account from any phishing attempts and preventing any outside program that may install fake apps and other such malware on your computer.
- Microsoft 365 Defender
This app is mostly used by organizations to protect themselves against any threats. It is backed by a global network of security experts who work tirelessly to protect your company’s data from any new or old attacker tools and techniques.
Besides directly employing the use of these tools, you can also follow these steps to protect yourself against any sort of hot wallet attacks out there:
- Lock hot wallets when you’re not trading anything
- Disconnect any of the sites that may or may not be connected to your hot wallet
- Always double-check the information before you copy and paste it
- Never store private keys in plain text
- Only use wallets that utilize multifactor authentication
- Terminate any and all browser sessions as soon as the transactions are finished
- Double-check any and all links to wallet websites or applications of this sort
- Always think twice before you go through with any hot wallet transactions
- Never allow any third party or wallet app developers to access your private keys or seed phrases
- Always use a hardware wallet, unless you need to specifically be connected to a device
- Always have file name extensions revealed on downloaded and saved files
The Security Measures of Guardarian

Guardarian is a non-custodial, fully legit exchange service that utilizes KYC and AML to ensure the fact that both the service provider and the client’s security during the transaction is taken care of. But what are KYS and AML and how can we trust our life savings on them? Let’s find out together.
- KYC, or Know Your Client, is a standard that essentially allows investment advisors to know everything that they need to know regarding their risk tolerance, investment knowledge, and of course, their financial position above all else. KYC simply put becomes the safety net that ensures that both the investment advisors and the client are going to walk out of the transaction happy with the result. In simpler terms, KYC represents an ethical and moral requirement that keeps both two parties involved in the process on equal grounds.
- AML or Anti-Money Laundering represents the process of verification that ensures the fact that both of the identities that the customers provided are legit. This process also forces the financial institutions to specify whether any risks may come from the transaction as a whole.
As a whole though, you can expect the following features to be found within the Guardarian’s security system: Speed, Simplicity, and Security.
To get through a transaction, you will simply need to go to the website, select the Fiat currency and the amount that you wish to exchange. Then, provide your phone number, and verify yourself by uploading a front and back picture of your passport, ID card, or residence permit. Afterwards, just go through facial verification and you can make the payment directly with a credit/debit card, or through a bank transfer.
Conclusion
Hopefully, the landscape will change for the better shortly as we would like to see a lot more security being added to the industry that so many of us have poured our life savings into.
Sadly, as time moves on it appears as though more and more malware and crypto attacking strategies will start to appear. To counter these, many websites will have to adapt and improve their security systems to make sure that both their clients and investment advisors can go through their transactions without any problems.
We will always try our hardest to confer your safety, we can promise you that much. As time moves on, we will always try to stay ahead of these cryware attacks and make sure that you can safely use our platform!